Although it varies by the surveys, in Japan today, about 20% of companies "permit", 30% "prohibit", and the rest "abandon" BYOD. Also in United States, 80% of the companies "permit", and less than 10% "prohibit".
It is absurd that using own Smartphone "totally private only" nowadays. Sometimes you might catch an incoming "call" from the company to your private Smartphone. Then you ought to be allowed "mail checking" while on business trip or in transport. In my own opinion, to start with 'reading and writing email (Webmail)', 'checking the schedule', and 'processing tasks through the Workflow (especially on draft-approval)' should be allowed. Workers want it as well.
In the first place, in this "age of cloud", work style is changing rapidly, today. At this moment, the world economy has been sluggish, so we the human race must work harder. A radical revision of the business ought to be carried out more often though the policy settings to suit the business type × industries × scale is required. The world's GDP will be certainly improved, if they aggressively permit for example, 'working during move' or 'working at own home'.
Anyway, you should avoid 'ambiguous BYOD' (leaving as is). It will be ended up with increasing of 'secretly act' which you don't know whether it is iniquity or not, such as forwarding company business mails, or duplicating business data to USB memory or to Dropbox and so on. Rather, you should let "right thing to do" to be known, and let it penetrate as a rule.
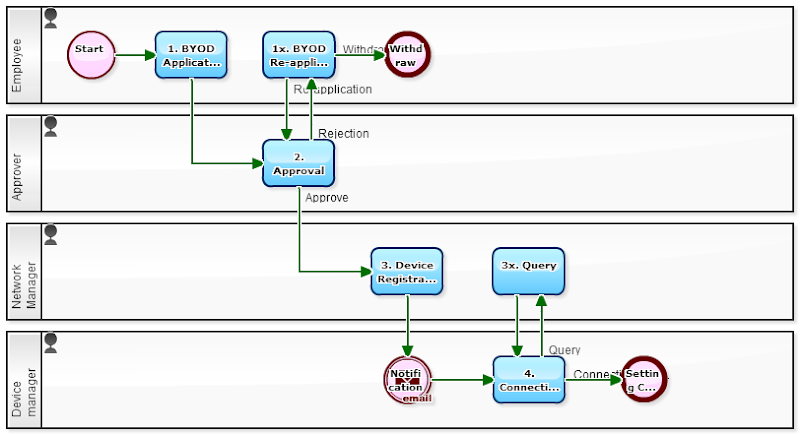
[BYOD Application flow]
[BYOD Application flow: "1. BYOD Application" screen]
This Workflow is for getting a permission of using company wireless LAN. In order to practice the "BYOD permission" as the first step of liberalization of work style, the company needs to grasp the communication device of workers use. For the timing to grasp the communication device, 'LAN connection request' is very convenient.
In the workflow above, the description of 'instructions on connecting wireless LAN' and 'BYOD Policy (things right to do / wrong to do)' when notifying 'the permission' is great. And wireless LAN settings would not be done many times. With the 'instructions on connecting wireless LAN', the troublesome setting would be done smoothly.
<Instructions on Connecting Wireless LAN>
1. Selecting Host
Because SSID is "Stealth", there is no notification from the wireless host. Enter 'xxxxssid' by yourself.
* SSID (Service Set ID) is a group name of the wireless LAN network.
2. Encryption setting
Supporting "WPA2-PSK" as the security scheme.
3. Password
Encryption Key Is "zzzzzzzz". Enter by yourself.
(Note, supporting protocol is "802.11a/b/g")
<BYOD Policy>
1. Supervisor's Permission
When workers to use personal information terminal devices such as Smartphones, clarify the purpose of use and the device, obtain the permission of the supervisor.
2. Self-pay
Maintenance costs and communication costs to be borne by oneself
3. Device Registration
When you get permission, report to the company to that effect.
4. Login Control
Secure the device with password, etc.. Biometric authentication is desirable.
5. Prohibition of Local Storage
You must not store Business data on your device permanently. If you need to save more than 30 days, requires the permission of the supervisor.
6. Immediate Reporting when Lost
You must report immediately to the company, when you lose or discard your device.
7. Reporting the End of Use
When you exit the business use, or the employment contract is terminated, report immediately company to that effect.
<Similar Models>
- Manage Strictly "MAC addresses" that Connect to Wireless LAN! (2012-04-30)
- Approval Flow that Decision-making Authority will be Delegated after 3 Hours (2012-11-12)
- When You Want ANYBODY to Give You That Approval (2011-01-25)
<<Related Articles>>
- [Rule] To Setup "Allocation Rule" to Applicant's Supervisor be Assigned
- [Rule] To Coexist Reversible Task and Irreversible Task
- [Auto Event] Make settings to automatically send an email to those in need of consensus-building
- Business Template: BYOD Application flow